TL;DR: IRCCloud now supports the IRCv3 Strict Transport Security draft.
We’ve always worked hard to ensure secure access to our service. For instance, we’ve enforced HTTPS in our web and mobile apps from day one. We were also early adopters of an HTTP Strict Transport Security (HSTS) policy that adds even stronger safeguards to secure connections, and our policy is now preloaded in all major browsers.
Employing strict security policies for access to our service is important because it protects users who might otherwise be using an untrusted internet connection. But until now, onward connections to IRC networks haven’t enjoyed the same degree of protection.
As mentioned in a previous post, we’re an active participant in the IRCv3 working group. Recently this has involved developing a Strict Transport Security (STS) mechanism for IRC. A first draft specification has now been published, and we’ve just enabled support in IRCCloud.
This means we’ll verify that IRC servers support STS, and always use secure connections with servers that do. Also, if an STS-enabled server fails certificate validation, we’ll refuse to connect and show errors like these:
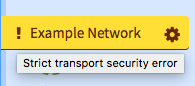


This is an important change. An invalid certificate can indicate that a secure connection has been compromised and is no longer secure. Previously, if you chose the “Secure port” option when joining a new network, we made sure to connect using TLS/SSL, but we wouldn’t inform you if any certificate errors are encountered. For servers without STS, we aren’t changing this behaviour straight away.
This decision was made because a significant number of IRC networks are set up to use free, self-signed certificates that can’t be validated. These networks are largely volunteer-run with no budget, but our users still expect to be able to connect to them. If we showed an error message on each of these connections, users would quicky learn to ignore security warnings.
However, that situation is gradually changing. With an increased interest in securing our communication channels, and the emergence of free certificate authorities such as Let’s Encrypt, we’re starting to see more IRC networks switch to validated certificates.
In light of this shift, and along with mandatory certificate validation for servers that use STS, we’ll be looking into ways to better surface certificate errors in future.
In the mean time, the IRCv3 STS specification is still being finalised, and you can keep track of its progress on GitHub.
 IRC
IRC